Multi-Party Computation (MPC), also known as Secure Multi-Party Computation, secure computation, or privacy-preserving computation, is a cryptographic technique that enables multiple parties to compute a function over their private inputs without ever revealing the inputs to each other.
Unlike traditional encryption, which secures data in storage or transit, MPC ensures data privacy even during processing.
In short, secure MPC technology does exactly what you would expect from the name: allow multiple parties to perform computations in a secure manner.
Recent advancements in MPC have improved its efficiency, making it feasible for large-scale applications. Companies and institutions are increasingly adopting MPC technology to enhance privacy in financial services, healthcare, and blockchain applications.
Multi-Party Computation (MPC) technology can be used to perform calculations in situations where private or confidential information is involved and needs to remain secret.
It provides a solution where businesses can work together and compute necessary outputs (like market prices or analytics) securely, while maintaining the privacy of their internal data.

Let’s say we have a group of people working in the same business and they’re interested in finding out what the average salary between them is. It’s useful information – after all, knowing whether you’re earning below or above the average could help with career decisions or salary negotiations.
Here’s the problem: Not everyone is comfortable sharing their salary. Money is personal, and many would not want to reveal their paycheck.
Fortunately, that’s not necessary, because we can just use Multi-Party Computation (MPC) to solve that problem. Instead of everyone revealing their salaries, MPC allows the group to securely calculate the average without exposing anyone’s individual number. It’s like magic – only it’s math. Privacy is protected, and everyone gets the insight they need.

Consider a scenario where several companies need to collaborate to set a market-clearing price for a product.
Here's the problem: The companies cannot reveal their individual costs or pricing strategies. In this case, each company holds private data that is essential to calculating the fair market price, but sharing this data directly would violate confidentiality agreements or competitive advantage.
Multi-Party Computation (MPC) allows these companies to compute the market-clearing price without disclosing their private data to one another. For instance, using MPC, each company would input its private cost data into a shared computation. The protocol would securely compute the price that balances supply and demand across all participants, ensuring no company learns the cost data of others, yet all can agree on a fair price.
The general theory of MPC was founded in the late 1980s and has since evolved into a practical technology used in areas such as privacy-preserving financial transactions, and collaborative machine learning.
In 1982, Andrew Yao introduced the concept of Secure Two-Party Computation (2PC) in his groundbreaking paper “Protocols for Secure Computations.” One of the most famous examples from his work is the Millionaires’ Problem, where two individuals want to compare their wealth without disclosing their exact net worth to each other.
To solve this, Yao proposed a cryptographic protocol that allows both parties to input their values, perform a secure comparison, and reveal only the final result – who is wealthier – without exposing any additional information. This concept laid the foundation for Secure Multi-Party Computation (MPC).
However, in 2008, the first large-scale and practical application took place, called the Danish Sugar Beet Auction. Ivan Damgård, a renowned cryptographer and co-founder of Partisia, played a key role in bringing MPC from theory to practice as one of the leading researchers behind the application.
In this auction, farmers and buyers used MPC to compute market-clearing prices without revealing their individual bids. This ensured fairness while maintaining the confidentiality of each participant’s pricing strategy.
The success of this event proved that MPC was not just a theoretical concept but could be used for secure computations in real-world business applications, paving the way for its adoption in different sectors and industries today.

Multi-Party Computation (MPC) might sound complex, but at its core, it’s a powerful way to compute results without exposing private data.
To understand how it works, let’s start with a simple black box analogy. Then, we’ll take a deeper dive into the mechanics behind it, exploring how MPC distributes and secures data to make it useless to hackers.
Picture this: We have four persons called Alice, Bob, Charlie, and Dorothy. They want to figure out the average salary between them.
To be a bit more precise, we’ll present Multi-Party Computation (MPC) as a black box and describe how the parties can learn their average salary between them by using this technology.

Each person sends their individual salary to the black box.
When all inputs are delivered, the black box will compute the average salary.
Only the result of the computation – the average salary – will be revealed about the inputs, not the individual salaries of the parties.
What is the problem that this black box solves? Why can’t the parties just hire someone outside the company (like a consultancy firm) to compute their average salary for them?
The key issue is trust. It’s not always possible to find someone outside the company, an external party, that all the participants trust and feel comfortable sharing sensitive data with.
This creates a “single point of trust” – a single person or entity everyone relies on to handle private information securely. Moreover, there’s also a “single point of failure”, because everything depends on that one entity and its tools functioning perfectly.
Using Multi-Party Computation (MPC) solves this problem by removing the need for a single trusted party. Instead of placing absolute trust in one party or system, MPC distributes the computation across multiple participants, ensuring that no individual entity can see the complete data. This setup eliminates both the single point of trust and the single point of failure.
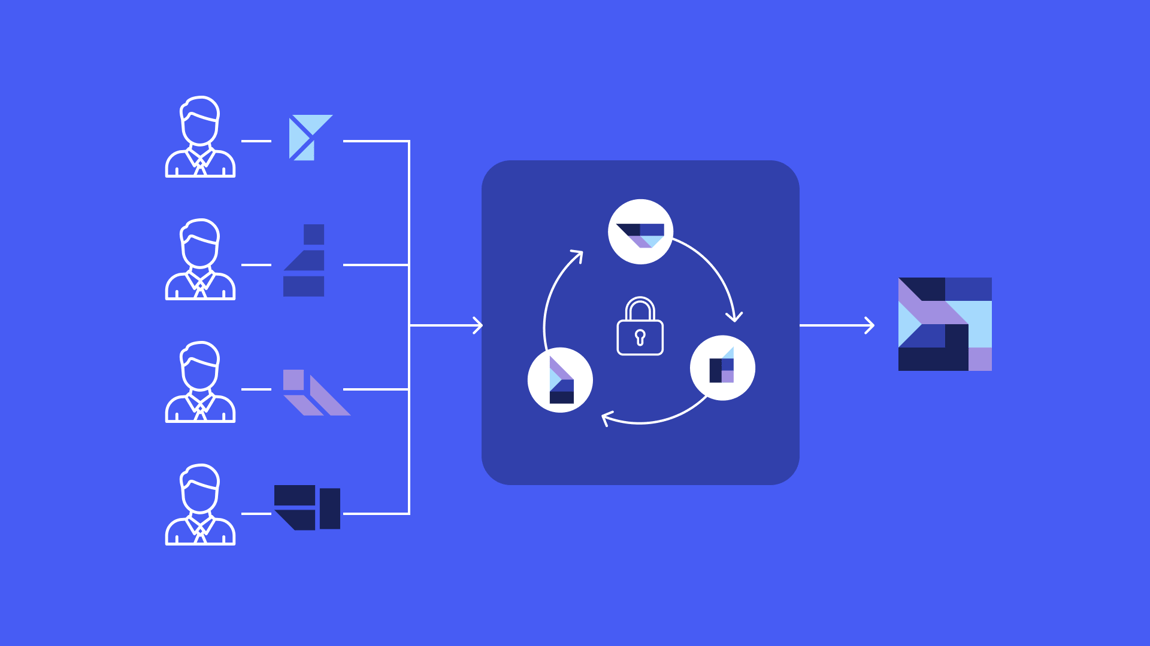
Let’s look closer at what is happening inside this black box. The salaries don’t just go into a black box and get blindly computed like a simple average calculator would. If that were the case, a hacker would only need to compromise a single machine to access all the raw salary data.

With MPC, information is decentralized. Instead of sending data to a single system, it's split into encrypted shares and distributed across multiple computing parties (as we can see in the graphic above). This means an intruder would have to hack multiple computers simultaneously to reconstruct any meaningful data.
In other words, MPC makes stolen data meaningless to hackers.
Therefore, the crucial advantage of MPC is that information is securely shared and encrypted across multiple devices, making it impossible for any single party to access the full data. In the end, only the final result is revealed – without ever having to trust a single person or system completely.
Watch Ivan Damgård, Chief Cryptographer and co-founder of Partisia, explain the complexities of Multi-Party Computing in simple terms.
Multi-Party Computation (MPC) has a wide range of applications across various fields, especially in industries like finance, healthcare, and government, where data privacy and confidentiality is critical. Here are some of its use cases.

Banks and financial institutions can collaborate on fraud detection models without exposing sensitive customer data.
Example: Multiple banks use MPC to securely analyze cross-bank transaction patterns, detecting fraudulent activity without sharing private user details.
Fintech's future: Privacy-enhancing tech & secure finance
MPC enables secure, real-time monitoring of suspicious transactions across institutions while maintaining compliance with privacy laws.
Example: Banks can work together to spot suspicious transactions without sharing customer account details, making anti-money laundering efforts more secure and private.
How banks can unite to improve Anti-Money Laundering detection

Hospitals and researchers can work together to study diseases and treatments without exposing private medical records.
Example: Multiple hospitals analyze how well a cancer treatment works, but patient data stays protected, following privacy laws like GDPR.
Revolutionizing clinical research with secure data sharing
Drug companies can combine test results from different trials without revealing who the patients are.
Example: A pharmaceutical company compares treatment results from different hospitals worldwide while keeping patient identities hidden.
The future of health data: A secure, decentralized approach to health data management

Governments can run digital elections where votes are counted fairly and securely, but individual choices remain private.
Example: A country uses MPC to aggregate election results, ensuring accuracy without exposing how each person voted.
Government agencies can study salary gaps, tax data, or population trends without accessing personal details.
Example: A city analyzes wage differences between men and women across industries while keeping individual salaries confidential.
Secure and scalable data sharing platforms explained

Companies can run procurement auctions where suppliers submit bids without exposing their pricing strategies to competitors.
Example: A retailer uses MPC to select the best supplier for a contract, ensuring fairness while keeping individual bid amounts confidential.
Manufacturers, suppliers, and retailers can collaborate on inventory and logistics without revealing proprietary information.
Example: A company securely verifies product deliveries across multiple suppliers without exposing exact shipment details to third parties.
Product traceability: How to build trust in your supply chain
The benefits of Multi-Party Computation (MPC) are particularly significant in scenarios that require data privacy, security, and trust. Here are the primary advantages.
A great benefit of MPC is its ability to process sensitive data while keeping it protected. The technology allows data to be handled and analyzed without revealing the individual inputs of participants. That means it is particularly useful for safeguarding private and confidential data.
MPC spreads computations across multiple parties, making it much harder for hackers to steal data. Even if one system is breached, the attacker only gets a small, meaningless piece of the data – not the full dataset.
MPC ensures that only the final answer – the computed outcome – is shared, never the raw or original data itself. This means sensitive information stays protected while still allowing for informed decisions.
MPC helps organizations follow privacy rules like GDPR, APPI, PDPA, HIPAA by allowing data to be used without exposing it. This means companies can get useful insights while keeping sensitive information protected.
MPC lets companies and organizations collaborate on data without revealing their private or sensitive information. This way, they can gain useful insights while keeping their confidential data safe and secure.
With MPC, there’s no need to rely on a single person, organization, or system to do things correctly or fairly when handling data. Each participant keeps control of their own information, making the process fairer and more secure while reducing the risk of misuse.
MPC works in such a way that no single component or participant's failure can bring down the entire system or compromise its functionality. There is no centralized server or single entity that holds all the data or control.
This decentralization ensures that even if one part of the system is attacked, corrupted, or unavailable, the rest of the system remains secure and operational. Multi-Party Computation (MPC): 5 quick insights from a Cryptographer on its growing potential
The applications of Multi-Party Computation are wide-ranging and have the potential to include all situations where private, confidential or sensitive information is involved. So, what’s next for MPC?
Ivan Damgård, co-founder of Partisia and the godfather of the early theoretical development of Multi-Party Computation, believes its application potential is huge.

Think about the history of digital signatures. They were invented back in the early 1980s, and back then that was a technology from outer space. Nobody understood what this thing was. Yet today, we are at a point where it’s used all over the place. Multi-Party Computation has that same potential.
Ivan Damgård
Chief Cryptographer, Partner and Co-founder of Partisia
Ivan Damgård acknowledges that understanding and implementing a new technology can take some time, and elaborates:
“Even politicians talk about digital signatures as if it’s something everybody understands. But that took 30 years. Multi-Party Computation is a much more complicated beast. So we have to give this time. We are on the way, but there is a long way to go.”
Peter F. Frandsen, Chief Operating Officer and Partner and Partisia, believes Multi-Party Computation represents a radically new approach to data usage, which requires a fundamental shift in people's mindset. Because it runs counter to conventional expectations, the technology must first be clearly understood before its full potential can be realized.

It’s a totally new way of thinking about, working with, and using data. People are not expecting that so first we have to make people believe that it can be done.
Peter F. Frandsen
At Partisia, we've already started revolutionizing the way companies are working with sensitive data today by implementing Multi-Party Computation technology in real-world business cases.
Explore some of our use cases:
Are you working in an industry where you're handling sensitive or private data and would like to utilize the full potential of the data?
Partisia Confidential Computing is able to do computation on encrypted data without ever breaching the regulations or privacy of the information. Download the whitepaper and discover how you can use Multi-Party Computation in your business.
